This article demonstrates how to configure Form – Based authentication using Active Directory step – by – step.
I.Create and configure a new Web Application
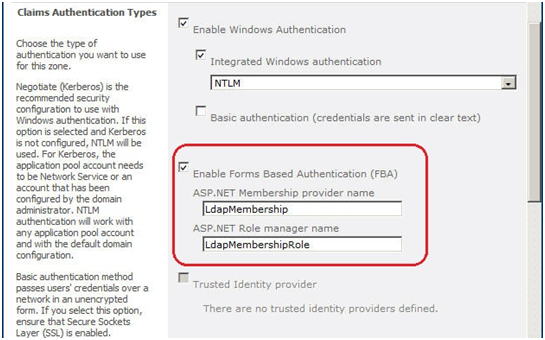
1. Select “Claims Based Authentication.”
2. Select “Enable Forms Based Authentication” and fill in the provider name and role manager name (Give any name you want, these two names will be used in web.config files later).
II.Configure web.config for CA and SecurityTokenServiceApplication
1. First, open IIS manager and find “SharePoint Central Administration v4” application and explore it.
2. Find web.config file, back it up first.
3. Open web.config again and find the “providers” section under the “roleManager” section and add following node:
<add name=”LdapMembershipRole”
type=”Microsoft.Office.Server.Security.LdapRoleProvider,
Microsoft.Office.Server,
Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c”
server=”your server name or ip”
port=”389″
useSSL=”false”
groupContainer=”OU=ou1,DC=sancheng08,DC=com”
groupNameAttribute=”cn”
groupNameAlternateSearchAttribute=”samAccountName”
groupMemberAttribute=”member”
userNameAttribute=”cn”
dnAttribute=”distinguishedName”
groupFilter=”(ObjectClass=group)”
userFilter=”(ObjectClass=person)”
scope=”Subtree” />
NOTE: It should look like this.
a. The attribute “name” should be the “ASP.NET Role manager name” that was specified previously when we created the Web Application.
b.?The attribute “groupContainer” should be the “distinguishedName” of the object that contains the users to be authenticated in Active Directory. “distinguishedName“ can be found in AD.
c. Here “OU=ou1, DC=sancheng08, DC=com” stands for Organizational Unit “ou1” in domain “sancheng08.com.”
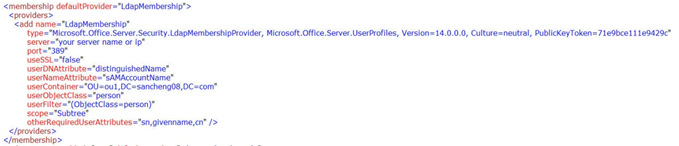
4. This time, find the “providers” section under the “membership” section, and add following node:
<add name=”LdapMembership”
type=”Microsoft.Office.Server.Security.LdapMembershipProvider,
Microsoft.Office.Server.UserProfiles, Version=14.0.0.0,
Culture=neutral, PublicKeyToken=71e9bce111e9429c”
server=” your server name or ip”
port=”389″
useSSL=”false”
userDNAttribute=”distinguishedName”
userNameAttribute=”sAMAccountName”
userContainer=”OU=ou1,DC=sancheng08,DC=com”
userObjectClass=”person”
userFilter=”(ObjectClass=person)”
scope=”Subtree”
otherRequiredUserAttributes=”sn,givenname,cn” />
a. The attribute “name” should be the “ASP.NET Membership provider name“ previously specified when creating the Web Application.
b. The attribute “userContainer” is the same as the attribute “groupContainer.”
NOTE: It should look like this.
5. Do the same for the web.config of “SecurityTokenServiceApplication.”
a. Under Connections -> Sites -> SharePoint Web Services, right click to Explore the SecurityTokenServiceApplication.
6. For the last step, modify the web.config of the application that we newly created previously.
a. Find “providers” under “membership” section and add provider:
<add name=”LdapMembership”
type=”Microsoft.Office.Server.Security.LdapMembershipProvider,
Microsoft.Office.Server, Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c”
server=”your server name or ip”
port=”389″
useSSL=”false”
userDNAttribute=”distinguishedName”
userNameAttribute=”sAMAccountName”
userContainer=”OU=ou1,DC=sancheng08,DC=com”
userObjectClass=”person”
userFilter=”(ObjectClass=person)”
scope=”Subtree”
otherRequiredUserAttributes=”sn,givenname,cn” />
NOTE: It should look like this.
7. Reset IIS after completing all the above steps.
8. The user can now be authenticated in Active Directory.